Your business computer's security system is only as strong as its weakest link, so make sure you know how to keep everything updated and secure. (Photo: iStock)
There’s an old saying about a chain being only as strong as its weakest link. That adage is no truer than in computer network security, where the criminals on the internet are constantly looking for easy pickings. At the basic physical layer of the network, it’s really just a chain of electronic devices, isn’t it?
All computers and all of the network devices that connect them — modems, routers, etc. — are made up of the same fundamental set of components: a processor (maybe more than one), some kind of data storage and an input-output channel. We can easily go down a rabbit hole on what devices use, which types of all of these, but for now let’s stick to the computers and mobile devices you use in the day to day operations of your business.
It’s a good bet that most of you are using Windows computers in your shops, with software and applications to manage your inventory, submit background check requests and maybe to run your point-of-sale (POS) terminal. I still call it a cash register, although at least one guy I know calls his a POS for good reason. But I digress.
The latest Windows operating systems from Microsoft, Windows7 and Windows10, are fine platforms for business use. They continue to be among the most popular and prolific systems used across the corporate spectrum. This popularity, however, is also why they are the most targeted systems by cyber criminals and other hackers in the “underweb.”
Apple computers are a lot less vulnerable to targeted exploits due to the tight requirements Apple employs for its internal developers and third-party application writers, and Linux (RedHat, Fedora, SUSE, etc.). While not as common as Windows in the business desktop world, Linux is somewhat more likely to be targeted due to its open source development approach. Anyone with the knowledge can write software for Linux, for better or worse.
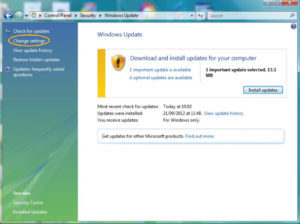
You can ensure that your Windows7 computer stays up to date by opening the Security section in your Control Panel and installing the latest patches. It’s safest to set the system to install them automatically while you sleep.
Those Weak Links
Vulnerabilities in your computer systems are constantly being discovered by the manufacturers, by industry researchers, and by the bad guys. The majority of these weaknesses are found and quickly patched before hackers develop a working exploit, but sometimes a mutt will find a hole before anyone else does and write up a hack for it. That’s called a zero-day exploit, meaning it can be used against the vulnerability on the same day it’s discovered, and they can be very destructive to both the computer and the business.
The risk from these vulnerabilities and exploits is identified simply as the point at which an existing vulnerability on a specific asset — your computer — encounters a specific threat, the exploit. Let’s look at how to minimize that risk.
Luckily there is a simple way to mitigate these risks on both your business computers and your mobile devices, and you already know what it is. Both Microsoft and Apple push out patches to their respective operating systems and their own applications. Microsoft generally sends its out on the second Tuesday of the month, while Apple doesn’t adhere to a set schedule.
In Windows7, the user still has options for how and when to install Microsoft patches. You can set it up to download them and install them later, just notify you when they’re available, or do everything automatically on the schedule you set. With everything else going on in your business, I recommend the automatic option, but set it to do it overnight.
Windows10 is a bit tighter in how it’s built. The user can only tell the system when to install updates. That’s a more effective way to do it, but, again, set it to run overnight and make sure you don’t leave any critical files or documents open the night it runs, because most of the time the computer will reboot after installation.
Did you notice I haven’t mentioned WIndowsXP? XP was a great improvement over the previous Microsoft systems, but it’s no longer supported with system patches, so please, pretty please with a cherry on top, if you’re still using XP, upgrade to Windows10. Most, if not all, of your applications will run just fine afterwards, but check with the publishers to make sure.
Apple computers have two main operating systems, macOS for desktop computers, like the iMac and portables like the AirBook, and iOS for their mobile devices, the iPhone and iPad families. They’re different animals, but for our purposes here they work the same say to update their respective platforms and applications.
The Apple Store is the channel through which Apple devices update the software installed on them. While Microsoft tells the user directly which patches are ready to install, or just does it, Apple publicly announces operating system updates to the tech press, through their owner support network, and sometimes to the mainstream media if the update addresses a major issue. When a new iOS version is ready, download and install it when it’s convenient, because it usually addresses security concerns as well as functionality. More on that later.
Most iOS apps are updated automatically through the Apple Store, and you won’t even notice. You might get a pop-up notification of what was updated, but that will be all. I’ve seen very few issues resulting from iOS updates on my devices, and the few that have come up have been resolved by Apple in the next build.
Now Android is a beastie unto itself. This operating system was designed by Google in the early 2000s and is based on the Linux operating system. It’s not really a true Linux system, though, but at its core it shares the same digital DNA.
The potential complication with Android is that, while computers from Dell, HP and Lenovo all run identical versions of Windows10, smartphones and tablets from Samsung, Motorola and LG don’t all run identical versions of Android. The underlying system may be very similar, but the interfaces can be very different.
I can tell you that the fundamental setup for any of these Android devices is the same: Go into the settings menu, and somewhere in there will be a variant of system updates for the operating system, and software updates for the installed applications. As with the Apple devices, the apps should update automatically, while the system itself requires your approval and scheduling.
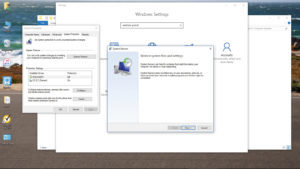
Computers running Windows7 and Windows10 have a built-in system failsafe called a Restore Point. Learn how to roll back your computer in the unlikely event that an update causes unintended consequences; it’s easy and pretty quick to return to the last known "good” configuration. (Photo: L.M. Larsen)
About Those Updates
Earlier I mentioned installing updates when it’s convenient. I need to clarify a few things in that area.
Sometimes — not often, but enough to warrant mention — a system update that you need will have those unintended consequences. Everything from slowing the device down to draining the battery faster, or even locking it up tight.
The raw truth is that sometimes, any of these manufacturers will push out a patch to address a specific issue, without fully testing every possible configuration of every device. With a Windows computer, there is a failsafe built in to the system to allow the user to recover from an update that went sideways.
In the Windows Control Panel, there is a security section that addresses Restore Points. These are snapshots created by the operating system before it makes a significant change, including patch installation. Check with your computer’s manufacturer on how to reboot to the last known "good" configuration, and you can restore your PC to full functionality, just as it was before the bad update. Microsoft will know about the bad patch, and will push out a corrected one soon after.
With Apple and Android updates, I have seen a very few that have caused serious issues, which is why I recommend waiting a week or so after they announce a new operating system update, just to make sure that the bugs are worked out before you install it.
Selfish? Yes. Practical? Absolutely!
One More Consideration
One last thing before we get back to business. Just as with the apps on your mobile devices, you need to make sure the third-party software on your business computers is kept up to date.

The intersection of your Assets, the Vulnerabilities within them, and the Threats targeting them define the Risk existing in your computer systems. Installing updates when they are published minimizes the vulnerabilities and therefore your risk.
Cyber criminals have historically come up with all kinds of creative ways to “weaponize” documents and data files used by software like Java, Adobe and web browsers. They can craft a file to take advantage of vulnerabilities within the software to force their way into the computer running it, and go from there to find and steal your sensitive information.
The publishers do their best to keep up with these threats and update their applications accordingly, but it’s up to the user to make sure that those updates are installed. Don’t automatically cancel the pop-up notice about updating your software installations; just do it and go get another cup of coffee while it runs.
As always, if you are unsure how or when to take care of any of these maintenance tasks, check with your computer manufacturer, the store you got it from or even your employee that knows about this stuff. You know you have one!
Like I keep telling my boss at work, if we keep doing the best we can at security on our systems, you won’t see a damn thing happen! But neither will the bad guys.






