One of the biggest threats to small businesses often comes from within; an employee who creates problems or commits crimes can destroy your enterprise.
Every school kid knows the name Benedict Arnold and the gist of his story — at least I hope they still teach American History these days. He was one of George Washington’s most trusted generals and advisors, until he started to believe the war was lost and decided to hedge his bets and defect back to the British. It didn’t help that his wife was a Tory and a British sympathizer, but that’s a story for another time.
There have been a number of other characters in our nation’s history who decided to sell or spill secrets to parties outside the country. The list of benefactors includes allies like Israel and France, enemies like the Soviet Union and other nations or groups whose relationships are still uncertain. Most of the time the motive is at least one of two drivers: political allegiance or money — though they’re often combined together.
In business, a true malicious insider — someone who uses position and access to obtain and sell corporate information for whatever reason — is thankfully pretty rare, especially in retail. I would bet real money that there has never been a gunshop employee who has sold a customer list to a competing store to hurt his employer. But there are a handful of other ways that you can be impacted by someone in your own organization acting irresponsibly or, worst case, intentionally trying to cause you pain because of some perceived insult, like a bad performance review or a cancelled contract.
Theft is Theft
Corporate espionage is generally thought of as more of a white-collar crime. I have worked a number of intellectual property theft cases in my career, all resulting from key people in companies stealing information on strategies or operations, then taking it to their new business to leverage as a competitor. I remember when I was a kid working in a local camera shop, going “undercover” to other shops to check their prices and inventories, but that’s just harmless competition. Wall Street calls it “business intelligence” when it doesn’t cause any harm to anyone.
A more recent trend in corporate security is what we call the “unwitting insider.” This is simply the poor computer user who falls for the bright, shiny phishing email and inadvertently lets the bad guys in through the back door. While traditional information theft still goes on in many industries, this is the most common intrusion vector these days, for two simple reasons: it’s stealthy and it works.
 As we discussed in the October 2017 issue of Shooting Sports Retailer, in a typical phishing attack, the bad guy crafts a very legitimate-looking email and sends it out to either a targeted list of recipients or, more likely, a larger list of email addresses bought from a source on the dark web, the criminal underground of the internet where these mutts buy and sell information, payment card numbers, passwords, etc.
As we discussed in the October 2017 issue of Shooting Sports Retailer, in a typical phishing attack, the bad guy crafts a very legitimate-looking email and sends it out to either a targeted list of recipients or, more likely, a larger list of email addresses bought from a source on the dark web, the criminal underground of the internet where these mutts buy and sell information, payment card numbers, passwords, etc.
The bogus email will often spoof a well-known insurance company, bank or popular website like eBay or Amazon, right down to using the same formatting and captured logos from the real websites. Most people are likely to fall for such an email, especially if they just give it a cursory look and don’t know what to look for.
Once the recipient responds by clicking on a link in the email, or by opening a document attached to the message, the virus or other “malware” coded into it will quietly launch, then start exploring the computer and network for the target data. After it finds and collects the data it’s looking for, the malware sends it back to the hacker, where he can use it, sell it or hold it for ransom from the business owner. All while the poor guy who opened the email is completely unaware that any of this is going on.
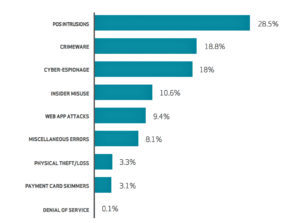
Let’s take a minute to look at a few statistics. Bear with me, you need to know this for background. For our purposes, the term “insider threat” refers to a trusted employee or vendor who has legitimate access but causes harm, regardless of intent.
In an article from May 2016, the Wall Street Journal referenced a Deloitte “Dbriefs” report in which they present some alarming numbers on corporate malicious activity by trusted insiders:
- 92 percent of insider threat cases were preceded by a negative work event, such as a termination, demotion or dispute with a supervisor.
- 97 percent of insider threat cases studied by Stanford University involved an employee whose behavior a supervisor had flagged, but that the organization had failed to follow up on.
- 25 percent of employees have used email to exfiltrate sensitive data from an organization.
There are other trends and statistics in the Deloitte report that relate to specific areas of operations in a business, but my point here is that a disturbingly high number of insider threat cases are caused by something going on with the person involved, that might have been caught before they happened. The email number surprised me, however, given how reliant we have become on email for communications throughout the day.
Most of us would never consider any of our employees to be a threat. We interview them, often check their references, run background checks and usually have them bonded for our own protection and that of our business. But human nature is unpredictable, and things happen that can cause them to react in ways they never would have considered.

Edward Snowden is considered a traitor by many.
Let’s look at a fairly recent high-profile insider case. Edward Snowden was a highly cleared contractor analyst in the intelligence community. At some point in the course of his daily work, he decided that he did not agree with certain things that his agency was doing, so he leaked a lot of classified information about it.
He considered himself a whistleblower, but the U.S. government calls him a criminal. Technically he did violate the agreement he signed when he got his clearance, but all these arguments are beyond our scope here. The point is that the information he released may have damaged ongoing intelligence operations.
That’s considered malicious.
Other insider threat cases over the years have included employees embezzling funds and cooking the books to pay for a loved one’s medical expenses, or using someone else’s computer login credentials to falsify emails to damage another’s reputation. There’s no one single profile for the insider threat; it can be anyone under certain stressors and circumstances.
So how do you, the business owner, reduce your risk of the insider threat within your organization? You’ve already done a lot of the leg work when you vetted your employees for hiring. Don’t stop there, though. The culture of your organization plays a huge part in your team’s mental health. If you’re a small firm, get to know your people — their families, their hobbies, what drives them to live their lives the way they do.
Learn their personalities and quirks. If there is a sudden change in their attitude or demeanor that goes on for more than a day or so, ask if they’re OK, if there’s anything they need. Don’t pry unless there’s a direct impact to operations, but if the culture is at least agreeable, there’s a good chance they’ll confide in you.
For a larger company, many health plans include Employee Assistance Plans that provide discrete counseling for life issues, usually at little to no cost to the employee. If you can offer troubled employees an outlet or avenue for assistance, it may deflect some bad decisions from them down the road.
Earlier I mentioned a scenario in which an employee used another’s computer login to send spoofed emails. There is a lot more that can be done with stolen credentials, especially when your financial or other business systems are involved.
This kind of risk can be reduced by implementing basic security practices — individual (not shared) user names and complex passwords (letters, numbers, characters) for every user and computer; limited user accounts on computers in sensitive departments, like accounting and human resources; and maybe even using multifactor authentication for those sensitive systems.
Vendors like RSA can provide tokens that are assigned to individual users and display a new alphanumeric code at timed intervals. To log in to a system with these devices, the user enters his username, password and that code. This greatly increases the likelihood that the credentials entered actually belong to the appropriate user they’re assigned to.
The RSA system can be pricey and therefore more appropriate to larger organizations, but there are other technologies at different price points, some of which use an app on Apple and Android smartphones instead of a token.
I wish I could tell you that the hardware and technical solutions we use to lock down our stores and networks will also protect your business against the insider threat, but the honest truth is that it is the most difficult to anticipate and therefore defend against.
Know your people. Educate them on e-mail situational awareness and the phishing threat, maybe even talk to them about their hopes and plans for their careers. If you foster mindfulness to these kinds of threats and ensure your people have healthy options when life throws them a curve, you greatly reduce your exposure to the insider threat.






